The Mcity Threat Identification Model is designed to help academic and industry researchers analyze the likelihood and severity of potential threats. Image Courtesy of University of Michigan Engineering
Latest News
January 15, 2018
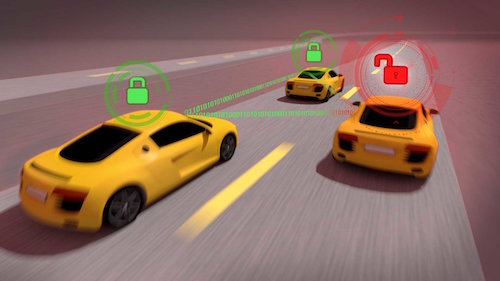
Cars can get stolen. Computers can be hacked. Self-driving cars may be stolen and/or hacked. “Assessing Risk: Identifying and Analyzing Cybersecurity Threats to Automated Vehicles” introduces a Threat Identification Model by Mcity, a public-partnership working to advance the development of autonomous vehicles. The report lays out a variety of other self-driving security hazards that the industry needs to address.
Mcity, a 32-acre mock city and test ground for autonomous vehicles located at the University of Michigan’s Ann Arbor campus, spearhead the framework to help academics and industry players analyze the likelihood and severity of potential security threats as they move forward on new designs. The framework takes into consideration the attacker’s skill level and motivation, the ways in which an attack could happen, any subsequent repercussions, and whether they’re related to privacy, safety, or financial loss, among other issues.
 Mcity is a public-private partnership working to advanced connected and automated mobility. Image Courtesy of Michigan Engineering
Mcity is a public-private partnership working to advanced connected and automated mobility. Image Courtesy of Michigan EngineeringSecurity in the age of the connected vehicle is a big deal. Autonomous vehicles are subjected to some variation of traditional cybersecurity threats such as data breaches of personal and financial information, spoofers that present incorrect information, or denial-of-service attacks. On top of those now standard risks, there are additional threats unique to this space that are not familiar territory for security experts working on the problem, Mcity researchers say. For example, hackers could take control over a vehicle and shut it down so it’s inoperable. It is also fairly easy, without the right protections, for a criminal to ransom a vehicle or its passengers, and even for a thief to take control of a self-driving car and relocate it to an area where it could become the next victim of a local chop-shop, the Mcity research found.
There are also possible security threats to the wide-ranging networks that connect automated vehicles, the financial networks used to process tolls and parking payments, as well as all of the roadway sensors, smart cameras, and traffic signals that will serve as infrastructure for connected vehicles, Mcity found. Autonomous vehicles also open up greater personal security risks: Consider that an autonomous car could be programmed to automatically unlock the door when you arrive at a certain distance from home, a move that could allow a hacker to use the vehicle to gain access to your home to initiate a burglary.
While the automotive industry has cybersecurity issues in its sights, the report contends that developers of automated vehicle technology are more focused on optimizing vehicle performance and may tend to overlook some of the more glaring issues. “To be truly effective, teams need dedicated members working on automated vehicle cybersecurity to handle the shifting issues and needs as the industry progresses to higher and higher levels of development,” the report noted. “Focusing on automated vehicle cybersecurity issues now is crucial to developing solutions that can expand and change to meet ever-increasing levels of automated driving.”
 The Mcity Threat Identification Model is designed to help academic and industry researchers analyze the likelihood and severity of potential threats. Image Courtesy of University of Michigan Engineering
The Mcity Threat Identification Model is designed to help academic and industry researchers analyze the likelihood and severity of potential threats. Image Courtesy of University of Michigan EngineeringTo help engineers and developers address security threats, the Mcity Threat Identification Model creates a framework that evaluates threats by:
- Threat agent, or the attacker, considering motivations and their capabilities to pull off an attack.
- Attack surface, meaning the potentially vulnerable components, including sensors, GPS systems, or databases receiving over-the-air updates.
- Attack methods—in this case, following the STRIDE classifications developed by Microsoft (Spoofing Identity; Tampering with Data; Repudiation; Information Disclosure; Denial of Service; and Elevation of Privilege).
- Also included in the model as part of the evaluation are attack potential (the difference between the threat agent’s ability to execute the attack with success and the system’s ability to withstand it), motivation, and impact such as potential loss to stakeholders.
Download the “Assessing Risk: Identifying and Analyzing Cybersecurity Threats to Automated Vehicles” white paper.
Watch this video to learn more about Mcity’s charter.
Subscribe to our FREE magazine, FREE email newsletters or both!
Latest News
About the Author
Beth Stackpole is a contributing editor to Digital Engineering. Send e-mail about this article to [email protected].
Follow DE