Vendors from around the globe presented hardware, software and services for the embedded technology market. English and German are both official languages for the conference. Image courtesy of Nürnberg Messe.
Latest News
March 5, 2018
At the recent annual Embedded World trade show and conference in Nuremburg, Germany, more than 30,000 attendees packed the aisles and visited more than 1,000 vendors. Both numbers set records for the 16-year-old show. Additionally, more than 1,700 attendees from 73 countries signed up for the added-cost conference program.
Embedded Technology and the IoT Marketplace
Embedded technology is a subset of the larger internet of things market, which continues to grow at a rapid pace. Research firm IDC estimated the global IoT market grew by 16.7% in 2017 to just over $800 billion and predicts global IoT industry spending to hit $1.4 trillion in 2021 as manufacturers and service industries continue to invest in the hardware, software, services and connectivity that enable the IoT. IT hardware maker Cisco estimates there will be 3.3 billion machine-to-machine (M2) connections worldwide by 2021, up from a current estimate of 1.5 billion.
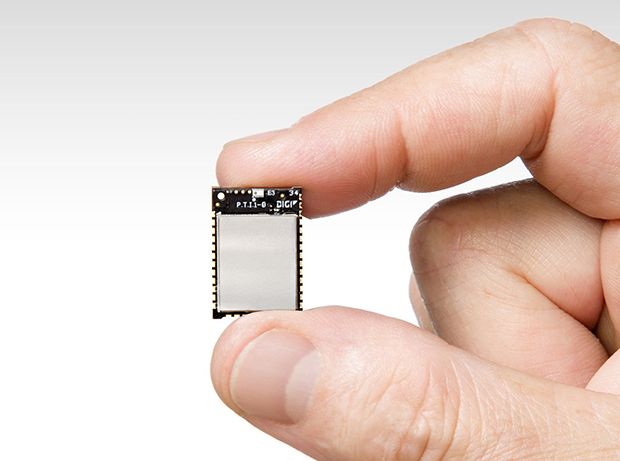 Digi xBEE 3.jpg: Controllers and embedded processors were in abundance at this year’s Embedded World. The new Digi xBEE 3 is half the size of its predecessor, supports Python programming, offers a dual-mode radio and can be upgraded via software to support Bluetooth LE. Image courtesy of Digi International.
Digi xBEE 3.jpg: Controllers and embedded processors were in abundance at this year’s Embedded World. The new Digi xBEE 3 is half the size of its predecessor, supports Python programming, offers a dual-mode radio and can be upgraded via software to support Bluetooth LE. Image courtesy of Digi International.“The discussion about IoT has shifted away from the number of devices connected,” notes Carrie MacGillivray, vice president for IoT and Mobility at IDC. “The true value of IoT is being realized when the software and services come together to enable the capture, interpretation and action on data produced by IoT endpoints.” IDC says the industry segments that attracted the largest investments for IoT development in 2017 included manufacturing operations, freight monitoring and production asset management. IDC predicts the top growth markets for IoT spending in 2018 will include airport facilities automation, electric vehicle charging and in-store contextual marketing.
Hardware spending on IoT is dominated by the modules and sensors that connect end points to networks, thus the reason 30,000 engineers crowded the aisles at Embedded World 2018 in Nuremberg, Germany, in late February.
There was the usual emphasis on making embedded devices safe and secure, as well as plenty to learn about emerging industry themes including autonomous computing applications, internet of things and embedded vision.
 Vendors from around the globe presented hardware, software and services for the embedded technology market. English and German are both official languages for the conference. Image courtesy of Nürnberg Messe.
Vendors from around the globe presented hardware, software and services for the embedded technology market. English and German are both official languages for the conference. Image courtesy of Nürnberg Messe.The increased use of embedded vision applications was a key topic this year. Computer vision is the use of digital processing to interpret meaning from video; embedded vision refers to the practical use of computer vision in machines, which understand their environment through visual means.
The arrival of powerful, low-cost and energy-efficient processors has made it possible to incorporate practical computer vision capabilities into embedded systems, says Jeff Bier, president of the Embedded Vision Alliance and a panelist at a well-attended session on embedded vision applications.
Bier says there has been “huge growth in awareness that vision is practical.” One key is that vendors have been assembling systems that simplify the specification of vision. “You can add visual to processing today without having to be a specialist engineer.” Embedded vision is a necessity for autonomous products, not just automobiles. Plants don’t need vision, but animals do, Bier noted; the difference is mobility.
IT vendors of all types have noted their world was rocked by the competitive pressure of smartphones, creating consumer expectations regarding all computer-mediated experience. The embedded vision industry is no exception. “Our customers ask why cameras in smartphones are better and cheaper than in embedded devices,” says Arndt Bake, chief marketing officer of Basler AG, a German provider of industrial cameras. “Smartphones pushed our industry.”
Two primary reasons for the perceived difference between camera quality in smartphones and industrial vision devices is longer product cycles and the need for more rugged products, notes Qualcomm’s Leon Farasati, who is director of embedded computing applications for Snapdragon, Qualcomm’s line of smartphone system on a chip (SoCs). Farasati says Qualcomm is working with manufacturers on ruggedizing Snapdragons for industrial applications and committing to extended lifecycles for selected chips. Qualcomm recently announced its Snapdragon 820 will be supported for industrial applications through 2025. “This change is required and is in response to industrial markets,” says Farasati.
Edge Computing
Powerful CPUs or SoCs will be needed as part of embedded vision as industrial applications become more complex, because there is too much data being generated to ship it all off to cloud processing. Such local processing is known as edge computing, and it was another key theme at this year’s conference.
AMD has become more competitive in recent years. The company was present at this year’s Embedded World conference to promote its new generation of computing devices as suitable for embedded use. AMD’s Chief Technical Officer Mark Papermaster presented one of the keynote addresses: “Evolving Embedded Systems in a Self-Directed World.” Four computing generations—mainframes, PCs, mobile and connected mobile—each brought disruptive change to manufacturing. Embedded computing is the next disruptive generation of IT, says Papermaster. “This is when tech seamlessly weaves into our lives.”
The new generation of machine intelligence is key to sophisticated embedded computing, Papermaster says. “Bring the data to the edge, and make it useful.” Machine intelligence in manufacturing will benefit process automation, reduce operating expenses, enable real-time and instant-response applications and open doors to entirely new applications.
A machine intelligence upgrade allowed agricultural products manufacturer Q Technology to move into automated food inspection using computer vision. In the past computer vision was limited to counting potatoes, says Q Technology’s Ricardo Ribalda, Ph.D. But their new processors allow automated inspection for quality, size, and disease or damage. Using open source software as a foundation for their machine intelligence efforts, Ribalda says their product development time “went from years to weeks.”
Papermaster noted that Q Technology’s upgrade is an example of applying “the neighborhood of computing” to industrial tasks. “Take the heavy lifting that has been sent to the cloud, and process it locally.” Connecting local nodes to a central cloud system is not disappearing, Papermaster says, but new software developments like machine learning and new hardware products allow for a significant increase in edge computing capabilities, to “process IoT data, run inferencing and analytics, and to perform data diagnosis” on-site instead of remotely.
Applying machine learning and artificial intelligence to embedded systems was also highlighted at another conference keynote presentation from IBM’s Andrea Martin, the CTO of IBM DACH. “Machine learning algorithms and new software will help us make sense of the vast and complex data gathered by billions of interconnected devices throughout the world.”
Internet of Insecure Things
Security must be at the heart of all edge computing applications, says AMD’s Papermaster. Rapid detection (popularized by “Hey, Google” types of voice direction) requires rapid identification. This means the security protecting such instant detection and authorization applications must be built in, processed on-site as fast as recognition.
But some in the embedded industry say security is not given enough consideration. Embedded systems consulting firm Barr Group was represented at the conference in panel discussions and presentations. Andrew Girson, Barr Group CEO, says his company’s research shows nearly 22% of embedded systems designers don’t have security on their to-do list. “Many design best practices that raise security levels aren’t being followed,” says Girson.
“This year’s survey confirms that products in development have become increasingly complex, for example, having more microprocessors aboard, which opens the door wider to opportunities for product malfunction,” says Barr Group Chief Technology Officer Michael Barr. “It is disheartening to see that many designers of safety-critical systems continue to skip software development steps that are known to reduce the number of bugs and unplanned behaviors in embedded systems.”
Systemic disregard for security is bigger than just potential loss of valuable data. Barr says 25% of all internet-connected devices are capable of killing or injuring people. “Of safety-critical embedded products currently in development, two out of three target the medical, industrial, automotive and defense/aerospace industries,” Barr says. “Moving forward, we hope that more developers will follow design practices known to be effective in maximizing the safety of end users.”
Blockchain Didn’t Get a Booth
One of the hottest tech topics in media right now is the cryptocurrency phenomenon. In product development, there is some discussion that the technological foundation for Bitcoin and other cryptocurrencies, the blockchain, has practical value for manufacturing processes. This may be the case, but blockchain was a no-show on the Embedded World trade show floor, and it was not the main subject for conference sessions, although several speakers at this year’s show have been considering it.
 Vendors from around the globe presented hardware, software and services for the embedded technology market. English and German are both official languages for the conference. Image courtesy of Nürnberg Messe.
Vendors from around the globe presented hardware, software and services for the embedded technology market. English and German are both official languages for the conference. Image courtesy of Nürnberg Messe.The blockchain is essentially a new form of establishing a data record of transactions that establishes trust without an intermediary. Blockchain records are immutable, notes AMD’s Papermaster, and that means huge files will be created, “and it doesn’t make sense to have that data out on the edges.” Papermaster sees embedded devices gathering, processing and sending data that becomes part of this new form of recordkeeping, but that the record itself will be stored elsewhere.
“Not everything makes sense to be placed on blockchain,” says Mark Patrick of Mouser Electronics, an embedded products manufacturer. “Only the parts of an application that particularly benefit from decentralized computing and authentication should be ‘blockchained.’”
The Barr Group has also been taking a close look at blockchain technology. “Embedded programmers often involve databases in their work, and you can think of blockchain as being a sort of a next-generation database with certain special properties,” says Barr. Because a blockchain is a distributed database with no centralized repository, it can open the door to new ways of using data.
Barr describes the example of how a specific car could be tracked. From initial assembly (such as the engine serial number), to firmware update records, to ownership changes and service records, everything about a specific automobile could be tracked in a trusted fashion. “And this is something that you would typically put into an environment where there are multiple different trust relationships—complicated trust relationships where you need an objective record of what has happened, say, in a series of transactions where maybe one party doesn’t trust another.”
More Info
Subscribe to our FREE magazine, FREE email newsletters or both!
Latest News
About the Author
Randall S. Newton is principal analyst at Consilia Vektor, covering engineering technology. He has been part of the computer graphics industry in a variety of roles since 1985.
Follow DE