Digital Security for the 3D Printing Supply Chain
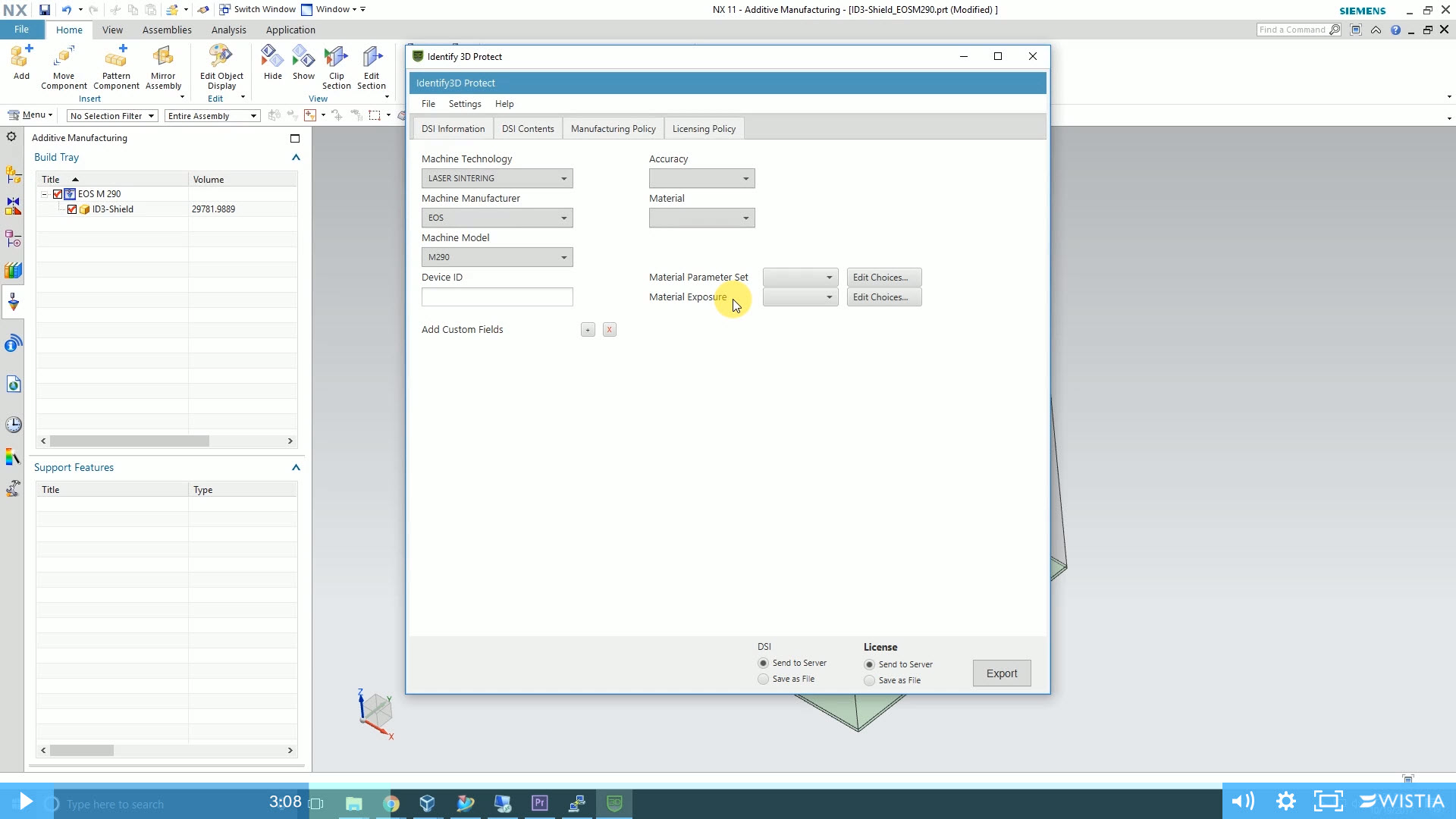
Identify3D Protect software, available stand-alone or in optional embedded format (shown here within Siemens NX design software). In this first of three software tools, users control design content, manufacturing policies and licensing policies within the digital supply chain of AM parts. (Image courtesy Identify3D)
Latest News
December 20, 2017
No matter the specific process, additive manufacturing (AM) can’t exist without a digital stream of data. From 3D CAD design through to final inspection, computer files define the intellectual property (IP) of the part itself, the build set-up, process settings, any monitoring steps, and complete provenance.
 Identify3D Protect software is available stand-alone or in optional embedded format (shown here within Siemens NX design software). In this first of three software tools, users control design content, manufacturing policies and licensing policies within the digital supply chain of AM parts. Image courtesy Identify3D.
Identify3D Protect software is available stand-alone or in optional embedded format (shown here within Siemens NX design software). In this first of three software tools, users control design content, manufacturing policies and licensing policies within the digital supply chain of AM parts. Image courtesy Identify3D.In this age of hacking and cyber attacks, manufacturers must consider whether this data is vulnerable to being stolen, misused or purposely corrupted. One company tackling this problem is Identify3D, founded in 2014 and about to launch a trio of targeted software tools in Q1 2018.
Stephan Thomas, co-founder/chief strategy officer, Identify3D, says he met Joe Inkenbrandt, the other company co-founder/CEO, at a business lecture. Thomas comes from a background of supply chains and operations and Inkenbrandt is experienced with IT security. Thomas notes, “I was fascinated by the potential supply-chain problems that AM could solve, i.e., the benefits of decentralized manufacturing, and Joe was already thinking about IP protection in additive.”
The two identified three areas of the supply chain—design, distribution and manufacturing—where digital security could play a major role, and began developing software to secure the end-to-end digital manufacturing solution.
Protect, Manage and Enforce
From the start, Identify3D has designed its products to work on the cloud or via on-site deployment. This means companies involved in defense work can use the software locally and thus maintain complete control. Thomas describes this option by saying, “We protect the data at rest, so it does not matter to us how the files move.”The three software tools—Identify3D Protect, Identify3D Manage and Identify3D Enforce—work together seamlessly but also separately. For example, says Thomas, “A design firm that does not manufacture would not need Enforce, or a manufacturer that does not design would not need Protect.”
Identify3D Protect enables designers to encrypt designs and couple them with business and production rules for AM. You create an encrypted digital supply item (DSI) package for each part, which has both a private section and a public section. The private section contains the build file, CAD file or any other intellectual property and is fully encrypted; it cannot be accessed until it is decrypted at the AM machine. The public section is where you can place images, documents and notes that anyone could view.
Next you set the manufacturing policy. For example, you can state that this part can only be built on a Renishaw AM500 machine, and choose available build parameters associated with that machine such as material, temperature and tray height. Third, under licensing, you enter an expiration date and authorized production quantity (e.g., someone can build 300 parts total and only through the end of December), and state which vendor will receive this authorization.
Lastly, you choose how the vendor will receive the encrypted DSI package and the license. All instructions can be saved to a file or to a server, so the user can choose the best method for disbursement (company centralized location, off-line system, email, etc.)
 Order-control page from Identify3D Manage Software, showing orders for different parts, and the authorization details of a specific order. Image courtesy Identify3D.
Order-control page from Identify3D Manage Software, showing orders for different parts, and the authorization details of a specific order. Image courtesy Identify3D.Identify3D Manage controls the second stage of the digital stream. When an order comes through, Identify3D Manage receives it, adds it to an order list, controls its distribution, and authorizes its access only to those users and systems who meet specific criteria. Following our example, the vendor would open up an instance of the software, select the job order, select the actual machine on which to build the parts and even (optionally) choose a designated operator if there is a particular person who handles that type of job well.
This software tool can run on the user’s choice of computer platform, perhaps one that already contains the vendor’s ordering system, or on a secured industrial PC (SIPC) which is attached and dedicated to the specific AM machine.
Finally, Identify3D Enforce (either on the SIPC or integrated directly in the AM equipment) verifies the license, decrypts the public and private information, creates a machine-specific build file, and transfers the instructions to that machine. If the user wants, a feature called Trace also captures all production data for each part, from the company and machine that made it, to the material used, to the temperature profile and other relevant build parameters during the production. Trace then sends an in-depth analytics report to the owner of the design, providing a complete audit trail.
Security for Any File Type, Any AM System
So far, Identify3D has announced collaboration agreements with Renishaw, two divisions of Siemens Digital Factory, EOS and Materialise, and will support these companies in their quest to protect customers’ digital IP, enforce production rules and provide end-to-end traceability. These groups see the value and necessity for efficient and secure data flow, especially in the era of Industry 4.0.A great aspect of the Identify3D products is that they will work for any file type and any AM technology, from powder-bed metal or plastic systems to material-jetting equipment to extrusion-types and more. Users customize each feature for their specific needs, down to the permitted composition of build material. The company is even exploring various technologies that will identify a part’s manufacturer and machine long after the piece has been placed in the field. One such approach would involve embedding chemical trackers in parts; other possibilities include use of RFID and serialization numbering.
Watch an overview of the Identify3D process below, and an example of the tools in use with an EOS M290 metal AM system here.
Subscribe to our FREE magazine, FREE email newsletters or both!
Latest News
About the Author
Pamela Waterman worked as Digital Engineering’s contributing editor for two decades. Contact her via .(JavaScript must be enabled to view this email address).
Follow DE