CeBIT Keynoter Focuses on Securing the ‘Things’ in IoT

Kevin Mahaffey, CTO of cybersecurity firm Lookout, explains how he hacked the Tesla Model S. Image via Kevin Mahaffey’s CeBIT presentation.
Latest News
March 21, 2016
In July 2015, two cyber security researchers demonstrated to a reporter at WIRED magazine how they could remotely control a Jeep Cherokee after having hacked the onboard entertainment systems to gain control of the vehicle. The wireless “zero-day exploit” led Chrysler to recall 1.4 million vehicles to update their security systems, at considerable cost to the Chrysler bottom line and a collective scary bother to its customers.
Kevin Mahaffey is on a crusade to make this incident a cautionary tale never to be repeated. As the founder and CTO of cybersecurity software vendor Lookout, Mahaffey and research partner Marc Rogers of CloudFlare conducted their own automobile hack soon after the Jeep Cherokee incident. In August 2015, they took on the Tesla Model S. As he explained in a keynote on security and the Internet of Things (IoT) at the CeBIT conference in Hanover, Germany, last week: “Of all the connected cars we could look at, we chose the Model S for one reason: It was architected from the ground up; it doesn’t have a legacy. This is not a car, it is a data center on wheels.”
 Kevin Mahaffey, CTO of cybersecurity firm Lookout, explains how he hacked the Tesla Model S. Image via Kevin Mahaffey’s CeBIT presentation.
Kevin Mahaffey, CTO of cybersecurity firm Lookout, explains how he hacked the Tesla Model S. Image via Kevin Mahaffey’s CeBIT presentation.The two went into the hack with a hunch: “We had the hypothesis [Tesla] would be doing a lot right in the car,” Mahaffey said. “So even though we tried as hard as we could to hack it, we hoped we could find things we could showcase, to say ‘here’s what they did really well.’”
As it turned out, Tesla did do many things right, from an IT security point of view, but not enough. The pair gained access to a variety of IT systems in the car, and accomplished enough of an exploit to cause Tesla to update the embedded software on the Model S.
After Mahaffey and Rogers notified Tesla of their breaches, the company quickly created software updates, which were sent over the cloud to all Model S vehicles, as if it were a routine action. Customers were not required to bring their cars in, Tesla didn’t have to spend time and money on services, and there was no real public relations fallout from the event.
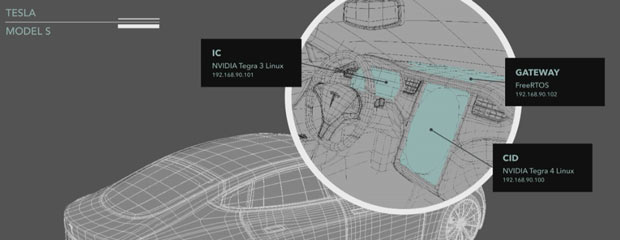 The Tesla Model S has three separate onboard servers. The Instrument Cluster (IC) and the Center Information Display (CID) run Linux; the Gateway runs FreeRTOS, a real-time operating system. All three are open source. Image courtesy of Tesla Motors.
The Tesla Model S has three separate onboard servers. The Instrument Cluster (IC) and the Center Information Display (CID) run Linux; the Gateway runs FreeRTOS, a real-time operating system. All three are open source. Image courtesy of Tesla Motors.Mahaffey said there are three crucial lessons to be learned from the Tesla Model S hack. These lessons apply to IT systems in general, but especially to the globally distributed IoT. These lessons are of vital importance because the industries creating the “things” in the IoT do not have a history in IT or cybersecurity. “It is easier to engineer [for security] at the beginning” during development rather than having to put patches in place to fix problems that are already in the wild, noted Mahaffey.
Lesson 1: Create a Strong Update Process
Computing devices require updates on a regular basis. IT vendors and their customers understand this; the mechanisms are in place for regular and (generally) painless upgrades. IoT devices are not immune to the need for software updates, but the ecosystem for software upgrades is not centralized, secure or commonly understood.
Mahaffey was adamant in his presentation about the need for updates to be engineered in, not added on. “[Software updates] need to happen frequently, they need to be free to the end user ... and they need to be one or two clicks, maximum,” he said. Consumers generally ignore software updates that are time-consuming or complicated.
Lesson 2: Create a Security-Immune System
All manufacturers must assume their devices will be attacked sooner or later. Most security newcomers engineer what they believe is a tight fortress of protection, to prevent the initial attack from gaining entry. “Big walls on the outside and nothing on the inside,” Mahaffey stated.To help manufacturers understand the importance of what he calls built-in immunity, Mahaffey offers the metaphor of the human body. Skin is just the first line of resistance from disease; every major system has its own method of dealing with infection. IoT security needs to be achieved on a system-by-system basis, not by trusting the external interface to be impenetrable. “Absolute trust will be hacked absolutely,” Mahaffey said. Harden each subsystem, and create sensors that monitor data transfers between systems in order to track what happens if a breach occurs.
Lesson 3: Isolate Critical Components
Returning to the body as an IoT metaphor, Mahaffey noted the most crucial system of all, the brain, has its own special layer of security, the blood-brain barrier. Carmakers and all others creating Internet-enabled devices need create their own blood-brain barrier around the gateway system. One example of an industry that “gets it” is commercial aviation.
“The in-flight Wi-Fi can’t talk to the autopilot,” said Mahaffey. “Your brake should not be able to talk to the Web browser; more importantly, your Web browser should not be able to talk to your brakes.”
The device gateway is the most important piece of the system, and needs the most preparation. You can’t rely solely on a great wall, Mahaffey noted, but a great wall is a great start.
More Info
Subscribe to our FREE magazine, FREE email newsletters or both!
Latest News
About the Author
Randall S. Newton is principal analyst at Consilia Vektor, covering engineering technology. He has been part of the computer graphics industry in a variety of roles since 1985.
Follow DE