3D Printing Ushers In Wave of New Cybersecurity Risks
AM used in a production capacity can be susceptible to design IP theft, counterfeiting and malicious operational interference. Here’s what some researchers and vendors are doing to mitigate risk.

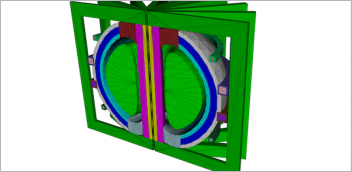
Rize’s inkjet technology allows QR codes, text, images and part numbers to be printed on the part, which promotes traceability and intellectual property control. Image courtesy of RIZE.
July 16, 2020
As 3D printing gains increasing support a feasible alternative to traditional manufacturing, it also creates opportunity for a wave of new cybersecurity risks, from theft of design intellectual property (IP) to malicious destruction of parts and planned system failures.
3D printing has been in the spotlight as the market incorporates new and more sophisticated offerings sporting novel printing technologies and advanced materials choices. At the same time, this next-generation of high-powered printers has been retooled to fit the needs of mainstream design and manufacturing engineers, from a cost and accessibility standpoint.
The result has been increased adoption of 3D printing for industrial-grade manufacturing use cases, not just as an instrument for rapid prototyping. According to Sculpteo’s 2019 State of 3D Printing report, more than half of respondents (51%) are applying 3D printing technologies for production and 63% believe the technology will play a significant role in a manufacturing and business context. Eighty percent of those responding to the Sculpteo survey said 3D printing has already had a significant improvement on their speed of innovation.
The escalation of 3D printing use for industrial-grade manufacturing means these processes are now prime targets for cybersecurity attacks. Just as enterprise systems and mobile devices opened up a Pandora’s box of security issues surrounding IT technologies, the transformation of design and manufacturing into a digital process creates similar challenges. Often, users and departments working with 3D printing technologies are unfamiliar with how to mitigate cybersecurity risks and are likely using products that haven’t been designed from the ground up with cybersecurity requirements in place.
“While companies are paying attention—especially if they’re looking at enterprise usage of additive manufacturing—like any new technology, it’s not fully understood by everyone in the enterprise,” says Andy Kalambi, president and CEO of Rize, a 3D printer manufacturer. “People may also not be cognizant of all the risks so they could end up with something untoward happening.”
Security Risks Are Many
The security risks of deploying AM for production of end-use parts and product assemblies is many. Confidential data, including schematics and other design IP, could be compromised as could personally identifiable information connected to an AM-produced individualized medical device like a prosthetic.
Digital files such as the 3D CAD model as well as the STL model file, sliced G-code file and build parameter data (each containing instructions to guide the 3D printing build operation) could be infiltrated. The breaches could translate into hard-to-detect structural defects that compromise product integrity, which in turn, could lead to other worst-case scenarios such as property damage, litigation or product recalls.
“The real challenge is realizing there is not just one cybersecurity challenge—there are lots of them,” says Jeremy Straub, assistant professor, Department of Computer Science and associate director for the Institute for Cyber Security Education and Research at North Dakota State University. “In a technology field growing and changing as much as additive manufacturing is, it’s difficult to anticipate everything that could represent a cybersecurity threat or other threats to the operation of the system.”
Deploying AM for product prototyping is a wholly different scenario than wielding the technology for production purposes, which then opens the door to various issues.
Simply put, Straub contends, the stakes are much higher. “With prototyping, the security issue is a throwaway compared to producing something that’s going to be used especially if safety is critical to the use case,” he says. “If someone gets access to a system that’s producing items going to consumers or a safety-critical industry, the potential for someone getting injured from a product is higher.”
The most common vectors for infiltration, according to Straub, are interfering with the 3D model supplied to the printer or messing with the printer’s actual operation. With the 3D model, an infiltrator could modify the fill pattern in a file so that it changed the thickness of a part wall or changed the shape slightly, typically in a way that would undetectable to the naked eye. Interfering with the printer’s operation could change the speed or layer spacing or modifying placement of the part on the build plate. All these modifications could affect the product’s structural integrity and cause it to break or cause danger to someone, Straub says.
Unlike conventional manufacturing processes like injection molding, 3D printing is more of a one-off process so the idea that if 99 parts print correctly, the hundredth one will as well isn’t a sure thing. “Probability works for more deterministic production processes, but it doesn’t work quite the same for bespoke production processes like 3D printing,” Straub says.
AM Security Solutions
Rize sees IP theft as the biggest security risk related to 3D printing. However, the firm contends its printers were built from the ground up to address security concerns due to the nature of its unique ink jetting technology, which allows QR codes, text, images and part numbers to be printed on a digital part. The ability to leverage such marking inks on a part—to deliver meta data, work instructions or assembly instructions—provides a level of IP control and establishes traceability and trust.
As a result, Kalambi says companies can better safeguard design assets, track what’s printed and determine whether a printed part is authenticated, which is especially important for protecting against counterfeiting. Kalambi likens the process to having the equivalent of a vehicle identification number (VIN) on every part.
“By printing the QR code, you can connect back into the model and every part is uniquely identified,” he explains. “It creates a digital thread between the 3D printed part and the model and that’s brought a lot of assurance for our customers.”
Siemens, which markets AM simulation software in addition to its Additive Manufacturing Network, an online order-to-delivery collaboration platform for industrial AM, is addressing the security challenges related to 3D printing in various ways.
Officials see the digitalization of the design-to-production process as creating new opportunities to address longstanding traceability issues, whether the production method is 3D printing or traditional practices like computer numerically controlled (CNC) milling, according to Aaron Frankel, vice president of Siemens’ additive manufacturing software program.
Early in the design cycle, users of NX can specify rules for CAD files that might dictate that a particular part design can only be 3D printed a specific number of times before it’s deleted and inaccessible. There is also the ability to digitally specify how a manufacturing plan should be executed on a printer with any diversions from that process plan automatically detected and flagged to operators.
As part of this approach, Frankel recommends separating the design and manufacturing policies into separate encrypted containers, making it more difficult to replicate during manufacturing.
“There’s an ability to trace and record what actually happens on a machine, creating and storing a file with the digital package,” he says. “When the part is delivered, the person on the receiving end now has a record of what happened during manufacturing so they can see it was made exactly as they specified.” Siemens has tapped the Identity3D digital rights management capabilities to deliver IP protection and to aid in manufacturing repeatability and traceability as part of its Additive Manufacturing Network platform and AM software suite.
Another emerging platform for secure 3D printing is Create it REAL, a platform that focuses on IP protection by allowing users to print without having direct access to the original 3D file. Create it REAL stores proprietary models as encrypted print files that are decrypted in real time by the company’s real-time processor and then 3D printed with the appropriate technology.
R&D Takes Aim at AM Security
In addition to vendor efforts, there is plenty of activity at the university and R&D lab level to address security issues related to AM. At North Dakota State University, Straub’s team is exploring how to apply quality assurance technology to ensure traceability and part integrity using an image monitoring system. The visible light sensing-based verification system is employed to detect discrepancies between expected and actual printed objects, helping companies identify discrepancies or flaws as the object is being built, not just at the end for verification, Straub explains.
“The idea of the QA system is that does most of the detection on its own, looking at what’s captured by the cameras and comparing them,” he says. “Humans can then do the final verification.”
At Indiana University-Purdue University Indianapolis (IUPUI), Jing Zhang is leading a research effort to explore a framework for accessing cybersecurity threats in the AM process as well as a proposed solution to the problem that zeros in on safeguarding CAD data to prevent both IP theft and any malicious and undetected modifications. In addition to proposing improved encryption on CAD data,
Zhang is promoting the use of 2D images to represent 3D models as way to safeguard design data. Deep residual networks can be used to learn a meaningful representation of the shape surfaces, enabling reconstruction of 3D shape surfaces at the end of the process for final AM part checks, he explains. The 2D image of the CAD model should be a match to the key 2D image sent along with it to establish key-based security, says Zhang, associate professor in the Department of Mechanical and Energy Engineering at IUPUI.
Traceability of 3D printed objects—whether to intercept counterfeiters or to track a specific 3D printed item back to a specific printer—is the focus of efforts at the University of Buffalo. The team, in collaboration with colleagues at Rutgers University and Northeastern University, have come up with the PrinTracker solution, which essentially can detect a unique “fingerprint” of a printer to aid in traceability. Their discovery was that 3D printed objects have in-fill patterns, which vary due to a printer’s model type, filament, nozzle size and other factors; this enables them to trace a printed object to the original printer source.
“Think about the 3D printing process as analogous to people’s handwriting,” explains Wenyao Xu,, associate professor of computer science and engineering at the University of Buffalo’s School of Engineering and Applied Sciences. “Different machines are going to fabricate the same product differently because of their own hardware properties and manufacturing processes. Each machine leaves a unique signature on the product.”
To prove their hypothesis, researchers printed five door keys on 14 common 3D printers, and using scans of the keys and an algorithm that calculated variations in the in-fill patterns, they were able to match the keys to the printers with 99.8% accuracy. The technology is not yet commercialized; to make it work, Xu says there would be a need to work with law enforcement to establish a registry of 3D printer fingerprints.
In yet another 3D printing security-related research effort, Carnegie Mellon University has come up with the Connected 3D Printer Observer (C3PO), which identifies a printer’s security vulnerabilities as well as potential attack paths based on given vulnerabilities and network deployment.
Georgia Institute of Technology’s School of Electrical and Computer Engineering, in partnership with Rutgers University, has developed a three-layer system that uses acoustic measurements, printer component tracking and detectable nanorods to protect the integrity of printed products.
While there are many possibilities for securing 3D printing, the bottom line is there is no singular solution. Rather, it will take a variety of technologies to adequately secure production-grade 3D printing throughout the full lifecycle. “There is no one solution to prevent the attack on the 3D printing process,” Zhang says. “It has to be a layered solution that will solve the problem from different perspectives.”
More RIZE Coverage
More Sculpteo Coverage
More Siemens Digital Industries Software Coverage
Subscribe to our FREE magazine, FREE email newsletters or both!
About the Author
Beth Stackpole is a contributing editor to Digital Engineering. Send e-mail about this article to [email protected].
Follow DE